Introduction
In today's dynamic and often unpredictable business environment, effective risk management is more critical than ever. Organizations must not only identify and evaluate risks but also develop robust strategies to mitigate them, ensuring resilience and continuity in operations. This comprehensive guide delves into the essential components of risk assessments, from defining scope and objectives to documenting and reporting findings.
It provides actionable insights and practical solutions for CFOs to navigate the complexities of risk management. By setting clear goals, employing advanced tools, and continuously updating risk assessments, companies can safeguard their stability and enhance their overall resilience, preparing them to respond swiftly and effectively to any crisis.
Defining the Scope and Objectives of Risk Assessments
Setting clear and specific goals for an investigation is essential to align all stakeholders and ensure a unified understanding of the objectives. This involves identifying key areas of concern, regulatory requirements, and specific incidents that triggered the investigation. For instance, organizations must account for incidents such as natural disasters, terrorist attacks, or health emergencies that could severely disrupt operations. A comprehensive evaluation of potential issues and business impact analysis, as emphasized by ASIS standards, form the foundation of this process.
Moreover, measurable objectives are essential for evaluating the success of the investigation. Efficient threat handling frameworks and control environments, as emphasized in conversations with specialists, should be clearly outlined to reduce possible dangers. It's also essential to include lessons learned and best practices from prior evaluations to improve future inquiries.
By establishing clear aims and quantifiable targets, entities can more effectively manage the intricacies of uncertainty, ensuring prompt and precise reactions to emergencies and improving overall robustness.
Identifying and Evaluating Risks
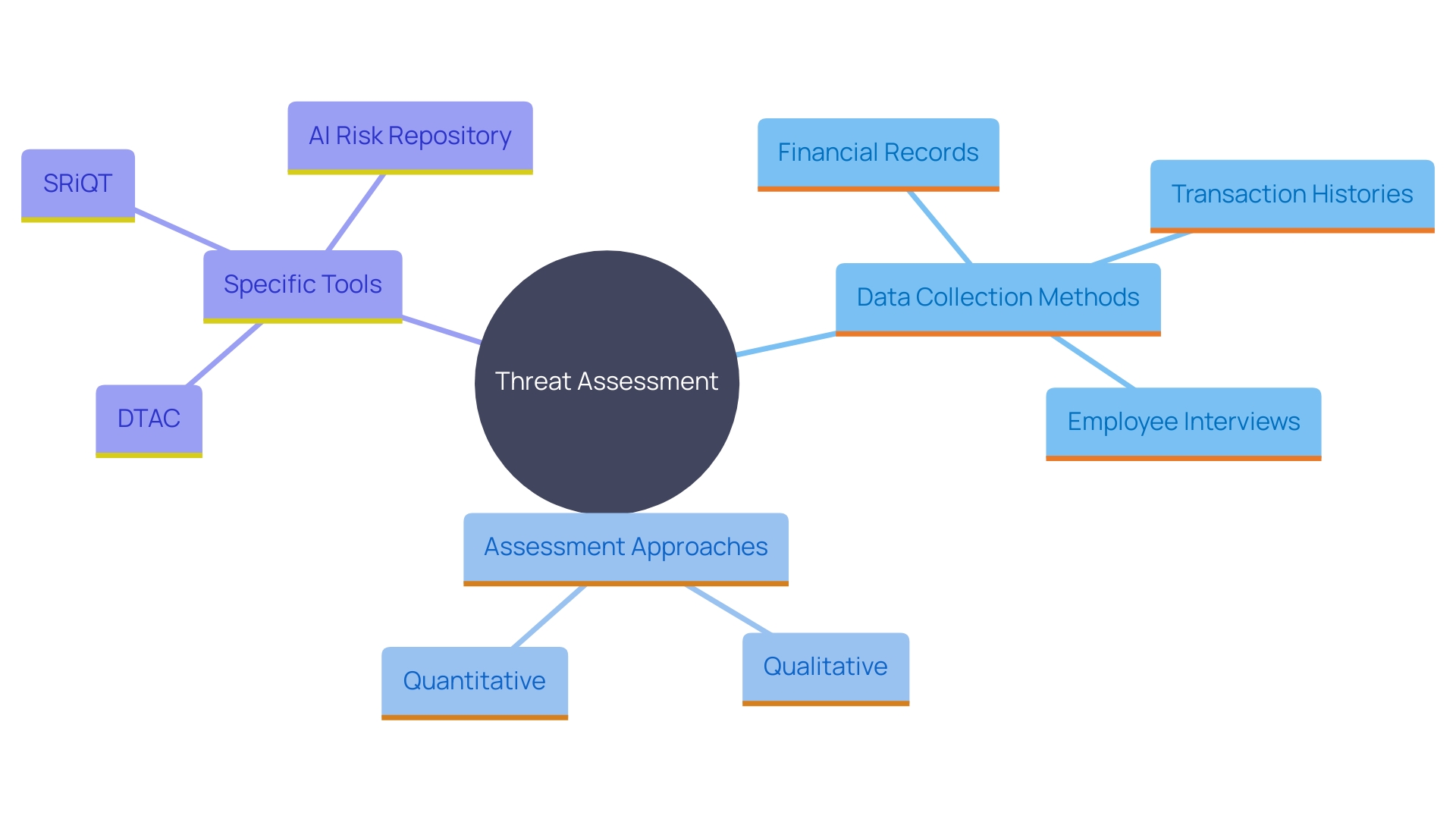
Carrying out a comprehensive assessment of potential threats is crucial for protecting an organization's stability. This process should begin with the collection of extensive data, encompassing financial records, transaction histories, and detailed employee interviews. The collected data offers a thorough perspective on the possible dangers. To accurately assess these uncertainties, it is crucial to employ both qualitative and quantitative methods. This dual approach guarantees a more comprehensive understanding of each threat's likelihood and potential impact, reducing the chances of overlooking significant dangers. For instance, advanced tools and frameworks, such as the Digital Technology Assessment Checklist (DTAC), can be utilized to assess compliance and technological maturity effectively. Furthermore, integrating data-driven structures such as Software Risk Quantification through Trust (SRiQT) can improve assessment precision by adjusting to the changing digital environment. The recent establishment of resources like the AI Risk Repository, which catalogues over 700 unique threats, is a testament to the importance of dynamic and updated evaluation methods. These tools and methodologies not only assist in pinpointing current dangers but are also invaluable in recognizing emerging threats, which, although not fully materialized, have the potential to significantly impact the business. As emphasized by the hazard control community, creating a forward-thinking strategy towards new threats through integrated danger technology can enable entities to handle and reduce challenges efficiently. By incorporating such extensive assessment methods, entities can more effectively maneuver through the intricacies of managing uncertainties and improve their overall robustness.
Developing Risk Mitigation Strategies
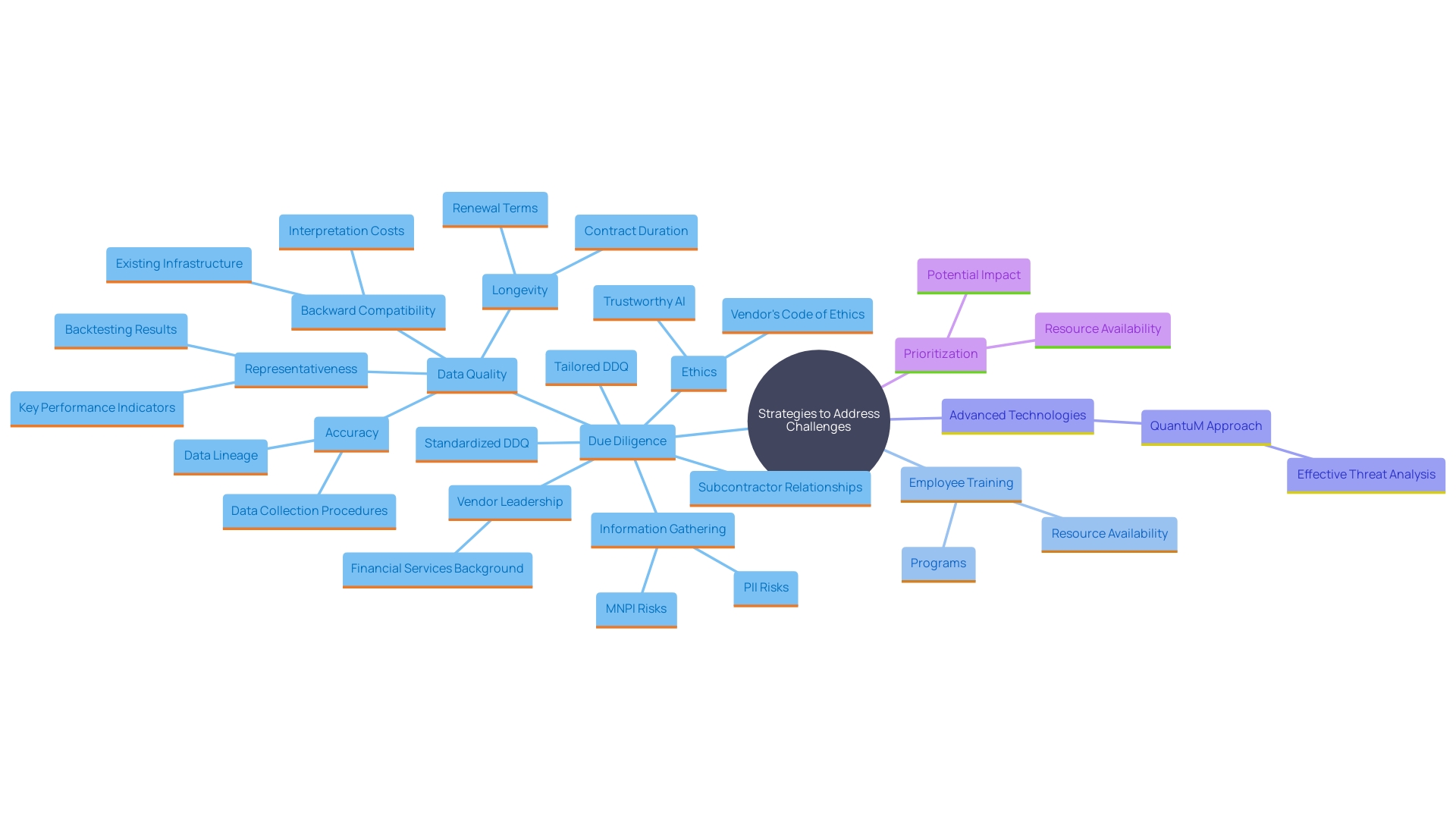
To effectively tackle identified challenges, it is essential to develop tailored strategies that address the specific obstacles your organization faces. This might involve the implementation of enhanced due diligence processes, comprehensive employee training programs, or the adoption of advanced technologies to monitor transactions. For example, M&T Bank, during its digital transformation, prioritized stringent regulatory compliance and the integration of robust security measures to protect sensitive data and ensure smooth operations. Likewise, utilizing artificial intelligence in credit evaluation has demonstrated to be a game-changer in preserving asset quality and fostering long-term growth.
The prioritization of these strategies should be based on the potential impact and resource availability, ensuring that the most crucial threats are addressed first. The QuantuM approach, for example, enables entities to analyze the financial loss linked to specific threats and assess the economic advantages of different security measures, thus improving threat analysis and prioritization. This method has shown great usability in real-world applications, such as a case study conducted in a Swiss SME.
In the banking industry, the focus on maintaining high-quality software standards and compliance is crucial to avoid expensive, time-consuming issues that can lead to security breaches and financial losses. By embracing a 'best-of-breed' strategy, companies can leverage a varied ecosystem of solutions to address their distinct challenges in overseeing safety, as emphasized in Kearney's PRISMTM supply chain safety advisory solution. Ensuring that the implemented strategies align with the organization's overall business strategy is key to achieving a comprehensive and effective risk management framework.
Documenting and Reporting Findings
Keep precise records of the investigation process, including thorough documentation of methodologies, information sources, and findings. This practice not only ensures transparency but also aids in substantiating the integrity of the research. For instance, consistent file naming conventions can help in tracking the history of documents through various stages of information cleaning, storage, and use, thereby demonstrating the veracity of information collection.
Prepare comprehensive reports that present findings in a clear and concise manner, making them easily accessible to stakeholders. This involves breaking down complex data into understandable insights, much like how the Washington State court data was effectively communicated to policymakers, prompting actionable feedback on issues affecting low-income domestic violence survivors.
Include practical suggestions that can assist the organization in reducing uncertainties and enhancing compliance in the future. For instance, comprehensive evaluations and oversight of new technologies, such as artificial intelligence, can avert weaknesses to criminal schemes. By adhering to these detailed and structured approaches, greater consistency, enhanced reliability, and increased impact can be achieved in forensic and investigative consulting services.
Reviewing and Updating Risk Assessments
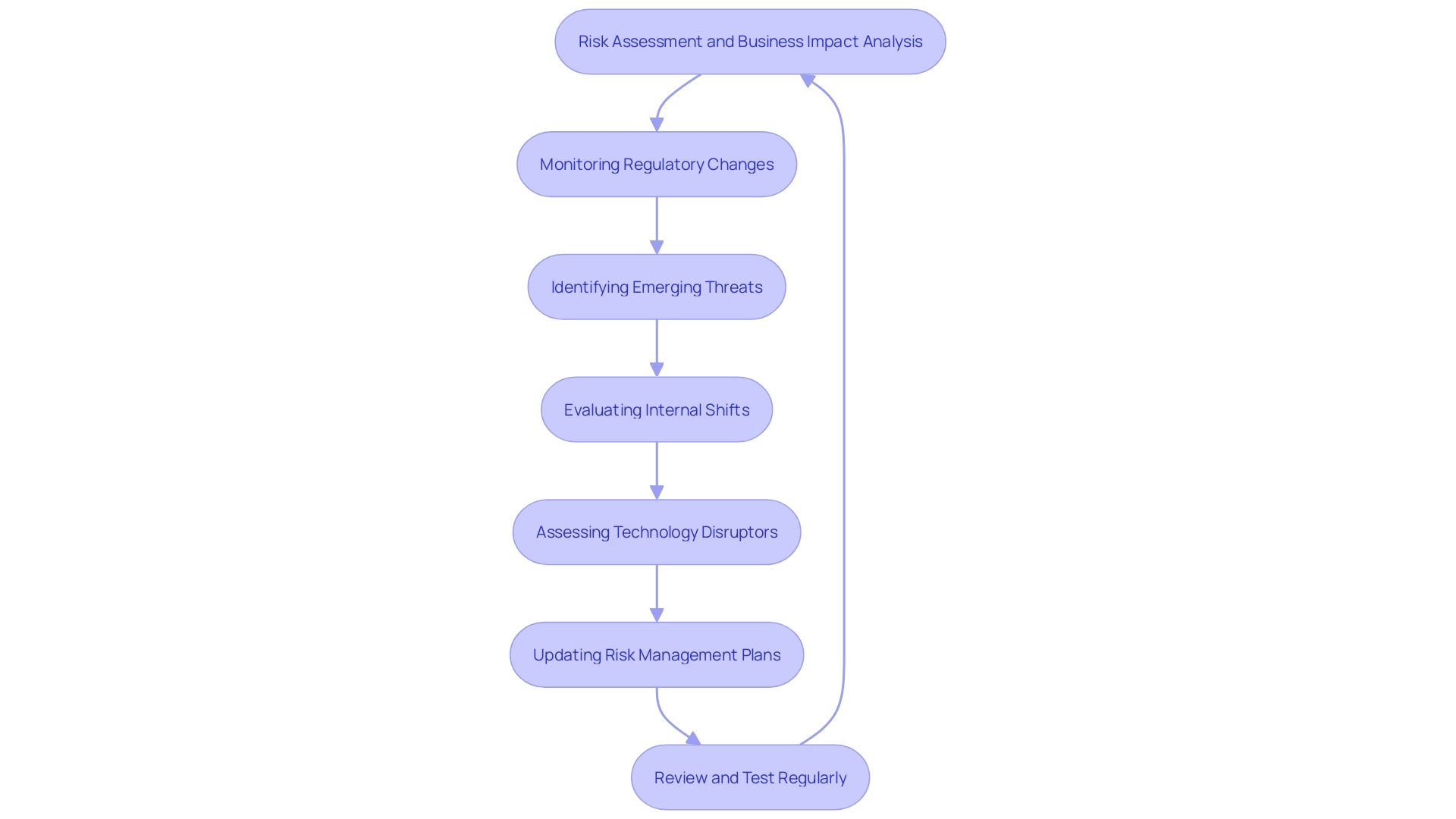
Regularly reassessing the effectiveness of hazard investigation strategies is crucial for maintaining organizational resilience. This involves keeping informed about regulatory changes, emerging threats, and internal shifts that influence vulnerability profiles. Ongoing enhancement is essential, as it connects management of uncertainties with changing business strategies and external circumstances. As per PwC's Global Risk Survey 2023, entities must assess technology disruptors as both threats and possibilities, ensuring their vulnerability landscape is examined during major transformations. Expert panelists emphasize that efficient evaluation methods are essential for adapting to new technologies and maintaining compliance. By consistently updating risk management plans, organizations can navigate uncertainties and capitalize on opportunities effectively.
Conclusion
In the complex landscape of modern business, effective risk management is paramount for ensuring organizational stability and resilience. Clearly defining the scope and objectives of risk assessments lays the groundwork for a unified approach, enabling organizations to identify critical areas of concern and establish measurable goals. This foundational step is essential for aligning stakeholders and preparing the organization to respond swiftly to potential crises.
Identifying and evaluating risks through comprehensive data collection and employing both qualitative and quantitative methodologies empowers organizations to gain a holistic understanding of potential threats. Utilizing advanced tools and frameworks, such as the Digital Technology Assessment Checklist and AI Risk Repository, enhances the accuracy of risk evaluations and ensures that emerging threats are not overlooked. A proactive stance towards these risks allows organizations to effectively navigate the complexities of the risk landscape.
The development of tailored risk mitigation strategies is crucial for addressing identified challenges. By prioritizing actions based on potential impact and resource availability, organizations can implement effective measures that align with their overall business strategy. This strategic approach, combined with meticulous documentation and reporting of findings, fosters transparency and enhances the reliability of risk management processes.
Finally, regular reviews and updates of risk assessments are vital for adapting to an ever-evolving environment. Staying attuned to regulatory changes and emerging threats ensures that organizations can refine their risk management strategies and seize new opportunities. By committing to a continuous improvement mindset, businesses can enhance their resilience and better prepare for future challenges.




