Introduction
In the rapidly evolving realm of mobile financial services, organizations face an unprecedented array of risks that demand immediate attention and strategic action. With cyber threats on the rise and regulatory landscapes shifting, it is imperative for leaders to adopt a proactive approach to risk assessment and management.
This article delves into the essential steps for initiating a comprehensive risk assessment, highlighting the critical role of:
- Stakeholder engagement
- Data analysis
- Robust cybersecurity measures
By understanding the complexities of risk in mobile financial services, organizations can not only protect sensitive information but also position themselves for sustainable growth in a competitive market.
Foundations of Mobile Financial Services Risk Assessment
Starting a mobile financial services risk assessment necessitates a strong understanding of your organization’s appetite and tolerance levels. Begin by recognizing key stakeholders, which should consist of:
- CFOs
- IT security teams
- Compliance officers
to ensure a comprehensive perspective on management. It is crucial to recognize the significance of utilizing third-party providers for monitoring and analyzing usage, as they significantly impact your risk landscape.
Collecting relevant information on current mobile financial operations is essential. For instance, leveraging Google’s analytics services necessitates an awareness of their privacy practices, as detailed in their policies (https://policies.google.com/privacy), to safeguard sensitive information. This reference is essential for understanding how these practices impact your overall evaluation.
The application of a structured framework, like the Risk Management Framework (RMF), allows for effective classification of threats across various areas, including operational and reputational challenges. Given the alarming statistic that 79 percent of higher education institutions reported ransomware attacks in the past year—often stemming from exploited vulnerabilities, which accounted for 40 percent of the root causes according to Sophos—it is essential to conduct interviews and workshops with team members to uncover potential vulnerabilities and threats. Documenting these findings meticulously will lead to the creation of a comprehensive mobile financial services risk assessment, serving as a solid foundation for further analysis and tailored mitigation strategies.
Additionally, with the cybersecurity market size estimated at USD 182.86 billion in 2023 and expected to grow to USD 314.28 billion by 2028, investing in robust cybersecurity measures, including PCI-DSS compliance for secure handling of payment information, is critical. By integrating all pertinent data points, threat signals, and customer information, leaders can develop a centralized response to effectively combat potential fraud and security breaches. The insights from the case study titled 'Healthcare Cybersecurity Insights' further emphasize the importance of adopting effective cybersecurity strategies to protect sensitive data.
Cybersecurity Considerations in Mobile Financial Services
In the swiftly changing environment of mobile monetary solutions, performing a mobile financial services risk assessment is essential. Begin by identifying potential threats such as:
- Data breaches
- Phishing attacks
- Malware
These threats have become increasingly prevalent. Significantly, a staggering 87% of educational institutions have reported experiencing at least one successful cyber attack, underscoring the urgency for conducting a mobile financial services risk assessment to implement robust security measures to protect sensitive financial data.
Evaluate the effectiveness of your existing security protocols and technologies, focusing on essential tools like:
- Encryption
- Multi-factor authentication (MFA)
- Secure coding practices
Conducting regular penetration testing and vulnerability assessments will help uncover weaknesses within your mobile applications and overall infrastructure. Furthermore, adherence to regulatory frameworks such as the Payment Card Industry Data Security Standard (PCI DSS) and the General Data Protection Regulation (GDPR) is paramount for ensuring data protection and minimizing liability.
Ensuring that third-party payment processors comply with PCI-DSS standards is crucial for the secure handling of payment information and protecting customer data. It is essential to convey the privacy policies of these third-party providers to customers, as transparency promotes trust and adherence. As highlighted by Cybersecurity Ventures, global spending on cybersecurity products and services is predicted to reach $1.75 trillion cumulatively from 2021 to 2025, reflecting the critical need for organizations to invest in security measures.
Additionally, the rights of individuals under the GDPR—such as access, rectification, cancellation, opposition, and the ability to withdraw consent—must be actively communicated to customers to foster trust and adherence. Organizations can achieve this through clear messaging in their privacy notices and during customer interactions. The global cyber attack on universities in March 2018, which targeted over 300 institutions and exposed 31 terabytes of data, serves as a stark reminder of the scale and severity of cyber threats faced by similar sectors.
As the cybersecurity landscape is continuously shifting, it is vital to keep your policies and training programs up to date, ensuring that all employees remain informed about the latest threats and best practices for safeguarding sensitive information. By adopting a proactive stance toward cybersecurity and conducting a mobile financial services risk assessment, organizations can significantly mitigate risks and enhance their resilience against evolving cyber threats.
Regulatory Compliance and Risk Management
To effectively oversee regulatory adherence in mobile monetary operations, CFOs must start by conducting a mobile financial services risk assessment to identify all relevant regulations that control their activities, including local laws and international standards. Key areas to focus on include:
- Data protection
- Anti-money laundering (AML)
- Consumer protection
Specific regulations such as PCI DSS and GDPR are critical in this context, as they provide frameworks for securing sensitive financial data.
Additionally, the integration of third-party service providers for monitoring and analyzing service usage can improve regulatory efforts. It is essential to ensure that these providers adhere to stringent privacy practices, particularly those outlined by Google, which emphasize the importance of safeguarding user data. These providers may offer analytics capabilities such as user behavior tracking and data reporting, which can further support regulatory initiatives.
Creating a thorough regulatory checklist is essential, enabling organizations to systematically address these critical areas. Significantly, as of 2024, regulatory frameworks for mobile financial services risk assessment are evolving, necessitating vigilance in adherence efforts.
Regular audits and reviews are vital for ensuring conformity to the mobile financial services risk assessment regulations. For instance, organizations overseeing adherence to PCI DSS and GDPR have demonstrated the effectiveness of ongoing evaluations in identifying gaps in regulation. The major breach of Target's point of sale systems in 2013, which compromised information of around 110 million customers, illustrates the real-world consequences of insufficient regulatory measures.
Maintaining meticulous documentation of all adherence efforts not only aids in internal accountability but also prepares the organization for any regulatory inquiries. Furthermore, engaging with legal and adherence teams can help your organization stay abreast of changes in the regulatory landscape, especially concerning mobile financial services risk assessment in the wake of recent data protection law updates affecting financial services. Employee training on regulation-related topics fosters a culture of accountability and empowers staff to uphold organizational standards actively.
As Tipalti, FinTech specialists, emphasized, grasping the landscape is essential; last year, up to 17% of adults with an annual income below $25,000 were unbanked, highlighting the significance of strong regulatory measures in reaching underserved groups.
Considering the concerning statistic that 87% of educational institutions have experienced at least one successful cyber attack, the necessity for robust protocols is reinforced. The cyber assault on more than 300 universities in March 2018, which revealed 31 terabytes of information, highlights the seriousness of cyber threats and the necessity of protocols in safeguarding sensitive data. Implementing multi-factor authentication, a practice adopted by 46% of organizations for securing remote access, can further bolster your organization's defenses against cyber threats.
By prioritizing these strategies and ensuring that third-party providers adhere to privacy practices, particularly those outlined by Google, CFOs can effectively navigate the complexities of regulatory compliance and enhance the resilience of their mobile operations.
Identifying and Mitigating Risks
To effectively start the mobile financial services risk assessment process, it is crucial to conduct a comprehensive analysis of your technology infrastructure, operational processes, and personnel. Utilize methods like SWOT analysis (Strengths, Weaknesses, Opportunities, Threats) and scenario planning to systematically identify potential challenges. This approach is particularly pertinent given that recent statistics indicate that endpoints are among the most targeted, with 81% of companies reporting malware infections on their devices.
As noted, 'endpoints are among the most targeted,' highlighting the critical need for vigilance. Additionally, phishing is the second most common vector for these attacks, utilized in 33% of cases. A case study on staffing and operational tasks in security operations centers (SOCs) underscores the importance of prioritization; despite 81% of respondents stating their SOCs are adequately staffed, security personnel spend 60% of their time on routine IT operations rather than security-related functions, indicating a misallocation of resources.
Once uncertainties are identified, prioritize them based on their likelihood and potential effect on your organization’s mobile financial services risk assessment. Create a comprehensive strategy for minimizing potential issues, outlining specific measures for tackling each threat, which may involve:
- Utilizing advanced technologies
- Improving training programs
- Setting up contingency plans
Organizations investing in MDR solutions have observed a 50% decrease in the difference of Mean time to detect and Mean time to respond, demonstrating the effectiveness of specific mitigation strategies.
Regularly review and update this plan to remain responsive to evolving threats and ensure its ongoing effectiveness.
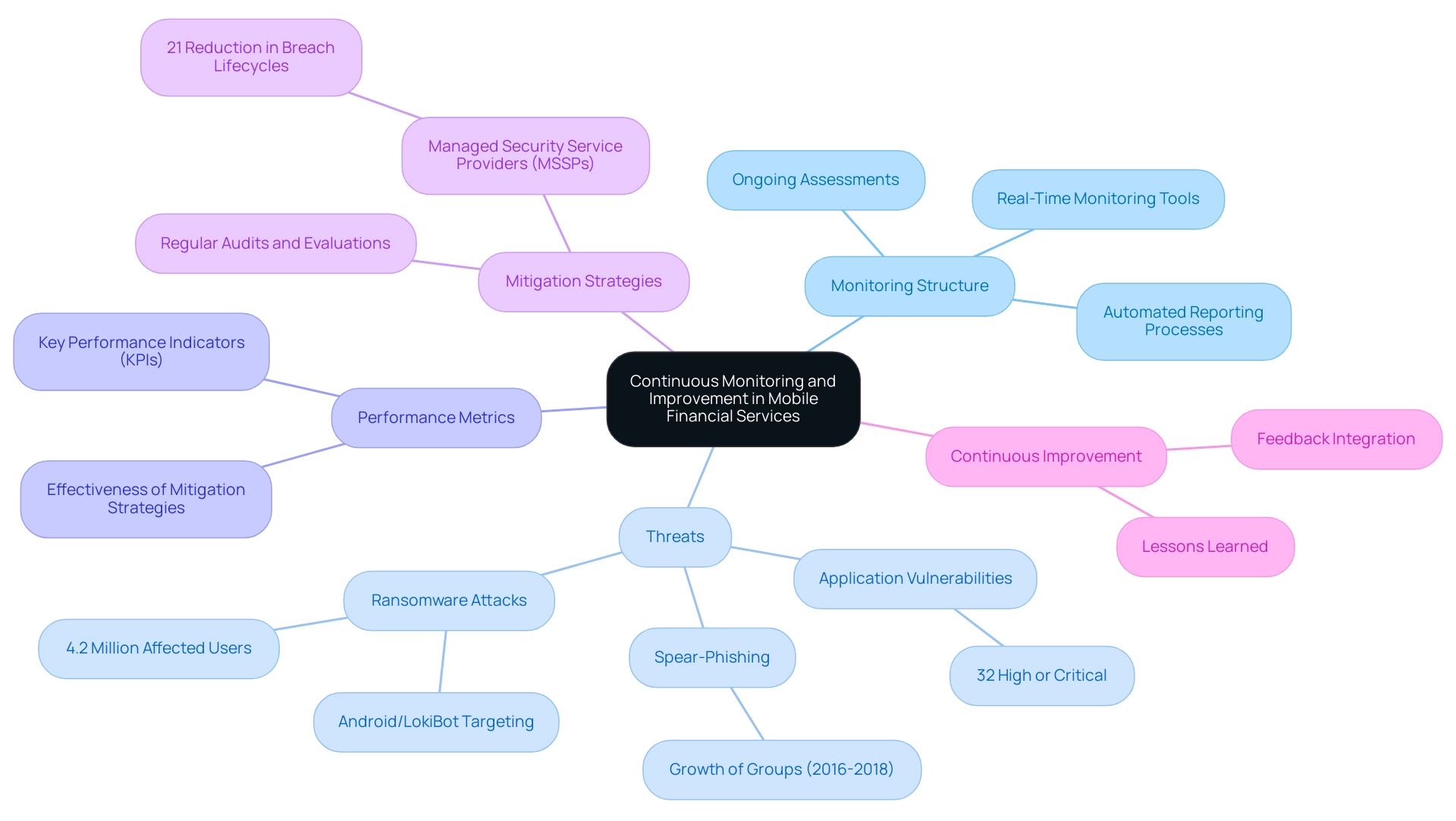
Continuous Monitoring and Improvement
To enhance your mobile financial services risk assessment, it is essential to create a strong ongoing monitoring structure. This involves regular assessments of management strategies and performance metrics, enabling you to stay ahead of emerging threats. Significantly, 32% of weaknesses in internet-facing applications are regarded as high or critical, highlighting the dangers linked to mobile banking services.
Utilize advanced tools and technologies that facilitate real-time monitoring of key performance indicators (KPIs), allowing for automated reporting processes that enhance efficiency. The rise of recognized spear-phishing groups from 2016 to 2018 further illustrates the evolving threats in the economic sector. Regular audits and evaluations should be carried out to measure the effectiveness of your mitigation strategies, including a mobile financial services risk assessment to ensure they are adaptive to the changing economic environment.
Furthermore, over 4.2 million American mobile users experienced ransomware attacks, with Android/LokiBot aiming at more than 100 banking institutions, emphasizing the real-world effect of these threats and the need for strong management strategies. Organizations leveraging managed security service providers (MSSPs) have experienced a 21% reduction in breach lifecycles, demonstrating the effectiveness of continuous monitoring practices. The recent trend shows that 57% of cloud SIEM deployments occurred in the past two years, driven by cost-saving measures, indicating a growing preference for cloud-based solutions that support operational efficiency.
By fostering a culture of continuous improvement and encouraging feedback from employees, stakeholders, and clients, you can integrate valuable lessons learned into subsequent risk assessments, ultimately enhancing your organization's resilience against financial threats.
Conclusion
In the face of increasing complexities and threats within mobile financial services, a proactive approach to risk assessment is not just beneficial; it is essential for organizational survival and growth. Engaging key stakeholders, leveraging data analytics, and implementing robust cybersecurity measures form the cornerstone of an effective risk management strategy. By comprehensively understanding the organization's risk appetite and utilizing structured frameworks, leaders can create a solid foundation to identify and mitigate potential vulnerabilities.
Furthermore, the urgency of addressing cybersecurity threats cannot be overstated. As evidenced by alarming statistics regarding successful cyber attacks across sectors, organizations must invest in advanced security protocols, adhere to regulatory standards, and maintain transparency with customers. Regular audits and continuous monitoring are crucial to ensure compliance and adapt to the ever-evolving threat landscape.
Ultimately, a commitment to ongoing risk assessment and management not only safeguards sensitive information but also empowers organizations to thrive amidst competition. By fostering a culture of continuous improvement and actively responding to emerging risks, leaders can enhance their resilience and position their organizations for sustainable success in the dynamic world of mobile financial services. Now is the time to take decisive action and prioritize comprehensive risk management strategies to secure a prosperous future.
Frequently Asked Questions
What is the first step in conducting a mobile financial services risk assessment?
The first step is to understand your organization’s appetite and tolerance levels, followed by recognizing key stakeholders such as CFOs, IT security teams, and compliance officers.
Why is it important to involve third-party providers in the risk assessment process?
Third-party providers play a significant role in monitoring and analyzing usage, which impacts your overall risk landscape.
What information should be collected regarding current mobile financial operations?
Relevant information includes understanding privacy practices of services like Google Analytics to safeguard sensitive information.
What structured framework can be applied in a mobile financial services risk assessment?
The Risk Management Framework (RMF) can be applied to effectively classify threats across various areas, including operational and reputational challenges.
What alarming statistic highlights the need for a mobile financial services risk assessment?
79 percent of higher education institutions reported ransomware attacks in the past year, indicating a high prevalence of cyber threats.
What are some potential threats that should be identified during the assessment?
Potential threats include data breaches, phishing attacks, and malware.
How can organizations evaluate their existing security protocols?
Organizations should focus on essential tools such as encryption, multi-factor authentication (MFA), and secure coding practices, along with conducting regular penetration testing and vulnerability assessments.
Why is PCI-DSS compliance important for third-party payment processors?
PCI-DSS compliance is crucial for the secure handling of payment information and protecting customer data.
What rights do individuals have under the General Data Protection Regulation (GDPR)?
Individuals have rights including access, rectification, cancellation, opposition, and the ability to withdraw consent, which must be communicated to customers.
What should organizations do to keep up with the evolving cybersecurity landscape?
Organizations should update their policies and training programs regularly to ensure employees are informed about the latest threats and best practices for safeguarding sensitive information.




